Downloadable Conditional Access System
Downloadable Conditional Access System or DCAS was a proposal advanced by CableLabs for secure software download of a specific Conditional Access client (computer program) which controls digital rights management (DRM) into an OCAP-compliant host consumer media device. The National Cable & Telecommunications Association (NCTA) proposed that DCAS be used as a substitute for physical CableCARDs, a standard also created by CableLabs for which products began appearing in August 2004 as part of industry compliance to the FCC mandate, which in turn is pursuant to the Telecommunications Act of 1996. DCAS is growing in popularity as a less expensive alternative for CableCARD, with major North American operator deployments from Cablevision[1] and Charter.[2] DCAS deployments can be expected to grow in the coming years, thanks to favorable regulatory view from the STELA Reauthorization Act of 2014[3] and FCC appointing a Downloadable Security Technical Advisory Committee,[4] and wider support for key ladder (K-LAD) functionality from system-on-chip (SoC) vendors and set-top box manufacturers.
DCAS in the early days, was a controversial proposal for a variety of reasons: it did not exist, had no set deadlines for support on all cable systems, no specification even in draft form was public, may not have satisfied FCC requirements that security modules be separable, and required an operating system (OCAP) that a majority of consumer electronics (CE) manufacturers did not wish to implement. The DCAS project was abandoned by CableLabs in 2009.[5]
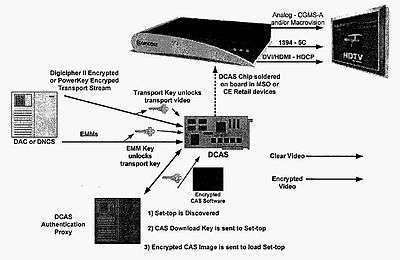
DCAS, as envisioned, removed the need for physical set-top boxes or CableCARDs to protect encrypted digital content. It was proposed that instead of a card with removable circuitry, a custom ASIC chip could be soldered onto the circuitboard of any digital cable-ready device. DCAS software would then run on this custom chip. Additional circuitry needed to run the OCAP operating system would be required. OCAP programs then would be used as the sole method of interacting with DCAS since it will enable cable companies to force the download of new security software. As set-top box ASICs have now advanced to SoC implementations, the minimum hardware circuitry to store key ladders (K-LAD) is embedded in the silicon, enabling much of the security functions to be implemented in software. Further, just as traditional set-top box functionality such as user-interface and middleware are moving to the cloud, DCAS enables much of the security functions also to move to the server side or the cloud. This allows thin client set-top boxes to be deployed that can be remotely managed, in lieu of the more expensive cableCARD based systems.
The basic purpose of DCAS was to implement DRM protection in software, supported by future OCAP-compliant consumer devices such as digital televisions, DVRs, and set-top boxes (still required to support legacy non-OCAP-compliant devices). This would secure the information transmitted in the link between the cable company and the consumer device. Besides decryption, the DCAS software would control how the content is used—whether it must be deleted immediately after viewing, or after a set period of time, which devices it may be transferred to and if transfer or recording is permitted. The scheme could possibly be used more broadly and was being advanced by Rupert Murdoch's company NDS as a DRM method useful also for portable media players and other devices not attached to cable networks. An allegedly working DCAS prototype was created by Samsung and NDS for the cable industry and was demonstrated to the FCC in November 2005.[6]
According to Brian Dietz of the National Cable & Telecommunications Association (NCTA):
...we expect downloadable security to be supported nationwide by MSOs by July 2008.
It was asserted by proponents that DCAS provided greater security for the cable industry because it allows them to change their entire security structure by downloading new software into host devices. If a particular encryption algorithm is cracked, it could be replaced by another one. Detractors noted that if the physical circuitry is compromised, it may not be replaced as is the case with CableCARDs. Some DCAS scenarios could use removable cards: OCAP-based devices may incorporate internal support for a kind of "smart card" (similar to the current SIM chip in a GSM cell-phone) to identify the subscriber and provide further protection. Proponents asserted that DCAS is more supportable since DCAS devices would not require a qualified technician to install the card. Detractors asserted that the final version of DCAS may require a physical card insertion, and that technicians are not required to insert CableCARDs anyway, since they are merely the same kind of cards that consumers routinely insert in their laptops. It was asserted that if cable companies were finally forced to agree on a standard for two-way communication that CableCARDs will be able to be remotely configured as would be the case with DCAS devices.
The expectation of the appearance of DCAS as a possible future technology was used as a reason that the FCC should release cable companies from obligations regarding CableCARDs. Verizon FiOS wished to be released from having to support CableCARDs at all on its network. Cable companies point to DCAS as a reason that they should be released from their obligation to use CableCARDs in their devices, as the FCC directed in 1998. The Consumer Electronics Association representing major consumer electronics manufacturers disagreed with these applications for waivers pointing to the insubstantiality of the proposal and that cable companies are notoriously late and half-hearted in their support of their own standards, as evidenced by their behavior with their earlier CableCARD proposal. Detractors of DCAS point out that the proposal is being used to sow fear, uncertainty, and doubt in the minds of consumers, CE companies, and the FCC. Consumers are motivated to hold off buying CableCARD devices, CE companies are wondering whether their CableCARD technology investments will soon be obsolete, and it causes doubt amongst FCC regulators whether they should enforce deadlines and restrictions placed on cable companies regarding CableCARDs. Detractors point to this as the latest in a decade-long set of delaying tactics that the cable company has used to avoid compliance with the Telecommunications Act of 1996. Cable companies counter that CableCARD devices have failed in the marketplace and that it would be foolish for them to be forced to use CableCARDs when the superior technology of DCAS will soon be available.
FCC mandate
The FCC has ruled that starting July 1, 2007, cable customers are to be able to purchase DVRs and other third-party devices to legally view digital cable without having to rent hardware from the cable company.
See also
- Interactive television
- Copy protection
- OpenCable Application Platform
- Conditional Access
References
- Cisco powers DCAS deployment at Cablevision, https://www.youtube.com/watch?v=DMJg53hy9jM
- Charter unveils Worldbox- Cisco key supplier of boxes with downloadable security, http://www.multichannel.com/news/technology/charter-unveils-its-worldbox/386685
- STELA Reauthorization Act of 2014
- FCC appoints downloadable security advisory committee, http://www.fcc.gov/document/appointment-members-downloadable-security-advisory-committee
- Jeff Baumgartner, MSOs Closing PolyCipher Headquarters, Light Reading Cable, (June 5, 2009), http://www.lightreading.com/document.asp?doc_id=177662&site=lr_cable.
- Implementation of Section 204
External links
- "OpenCable / DCAS". CableLabs. Archived from the original on 2006-03-26. Retrieved 2006-06-05.