KW-26
The TSEC/KW-26, code named ROMULUS, (in 1966 the machine based encryption system was not code-named "Romulus," rather the code-name was "Orion," at least in the US Army's variant) was an encryption system used by the U.S. Government and, later, by NATO countries. It was developed in the 1950s by the National Security Agency (NSA) to secure fixed teleprinter circuits that operated 24 hours a day. It used vacuum tubes and magnetic core logic, replacing older systems, like SIGABA and the British 5-UCO, that used rotors and electromechanical relays.

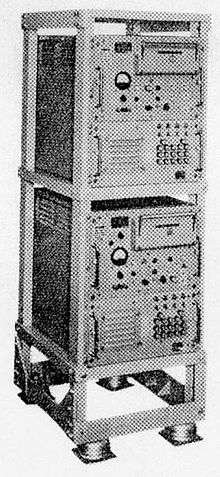
A KW-26 system (transmitter or receiver) contained over 800 cores and approximately 50 vacuum-tube driver circuits, occupying slightly more than one half of a standard 19-inch rack. Most of the space in the rack and most of the 1 kW input power were required for the special-purpose vacuum tube circuits needed to provide compatibility with multiple input and output circuit configurations. The military services' requirements for numerous modes and speeds significantly increased costs and delayed delivery. NSA says it is doubtful that more than three or four of the possible configurations were ever used.
The KW-26 used an NSA-developed encryption algorithm based on shift registers. The algorithm produced a continuous stream of bits that were xored with the five bit Baudot teleprinter code to produce ciphertext on the transmitting end and plaintext on the receiving end. In NSA terminology, this stream of bits is called the key. The information needed to initialize the algorithm, what most cryptographers today would call the key, NSA calls a cryptovariable. Typically each KW-26 was given a new cryptovariable once a day.
NSA designed a common fill device (CFD), for loading the cryptovariable. It used a Remington Rand (UNIVAC) format punched card (45 columns, round holes). The operator inserted the daily key card into the CFD and closed the door securely, locking the card in place. Decks of cards were created by NSA and sent by courier. The cards were strictly accounted for.
Because the KW-26 used a stream cipher, if the same key card was ever used twice, the encryption could be broken. To prevent re-use, the card was automatically cut in half upon reopening the CFD. As the units aged, the card reader contacts became less dependable, and operators resorted to various tricks, such as hitting the card reader cover with a screwdriver, to get them to work properly. Card readers were cleaned and the spring loading of the contacts checked as part of the routine maintenance of the device.
Because the KW-26 sent a continuous stream of bits, it offered traffic-flow security. Someone intercepting the ciphertext stream had no way to judge how many real messages were being sent, making traffic analysis impossible. One problem with the KW-26 was the need to keep the receiver and transmitter units synchronized. The crystal controlled clock in the KW-26 was capable of keeping both ends of the circuit in sync for many hours, even when physical contact was lost between the sending and receiving units. This capability made the KW-26 ideally suited for use on unreliable HF radio circuits. However, when the units did get out of sync, a new key card had to be inserted at each end. The benefit of traffic-flow security was lost each time new cards were inserted. In practice, operational protocol led to the cards being replaced more often than was desirable to maintain maximum security of the circuit. This was especially so on radio circuits, where operators often changed the cards many times each day in response to a loss of radio connectivity. In any case, it was necessary to change the cards at least once per day to prevent the cypher pattern from repeating.
Early KW-26 units protected the CRITICOMM network, used to protect communications circuits used to coordinate signals intelligence gathering. The initial production order for this application, awarded to Burroughs in 1957, was for 1500 units. Other services demanded KW-26's and some 14000 units were eventually built, beginning in the early 1960s, for the U.S. Navy, Army, Air Force, Defense Communications Agency, State Department and the CIA. It was provided to U.S. allies as well.
When the USS Pueblo was captured by North Korea in 1968, KW-26's were on board. In response, the NSA had modifications made to other units in the field, presumably changing the crypto algorithm in some way, perhaps by changing the shift register feedback taps. Starting in the mid-1980s, the KW-26 system was decommissioned by NSA, being replaced by the more advanced solid-state data encryptor, TSEC/KG-84.