Simon (cipher)
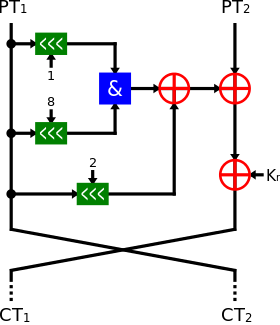 One round of Simon | |
| General | |
|---|---|
| Designers | Ray Beaulieu, Douglas Shors, Jason Smith, Stefan Treatman-Clark, Bryan Weeks, Louis Wingers NSA |
| First published | 2013[1] |
| Related to | Speck |
| Cipher detail | |
| Key sizes | 64, 72, 96, 128, 144, 192 or 256 bits |
| Block sizes | 32, 48, 64, 96 or 128 bits |
| Structure | Balanced Feistel network |
| Rounds | 32, 36, 42, 44, 52, 54, 68, 69 or 72 (depending on block and key size) |
| Speed | 7.5 cpb (21.6 without SSE) on Intel Xeon 5640 (Simon128/128) |
| Best public cryptanalysis | |
| Differential cryptanalysis can break 46 rounds of Simon128/128 with 2125.6 data, 240.6 bytes memory and time complexity of 2125.7 with success rate of 0.632.[2][3][4] | |
Simon is a family of lightweight block ciphers publicly released by the National Security Agency (NSA) in June 2013.[5][1] Simon has been optimized for performance in hardware implementations, while its sister algorithm, Speck, has been optimized for software implementations.[6][7] Security researchers have warned against the algorithm for potentially having a backdoor which would compromise the effectiveness of the algorithm, completely nullifying it. The privacy concerns came after NSA failed to give detailed technical details to the researchers from ISO, thereby standardization of this algorithm has not taken place. [8]
Description of the cipher
The Simon block cipher is a balanced Feistel cipher with an n-bit word, and therefore the block length is 2n. The key length is a multiple of n by 2, 3, or 4, which is the value m. Therefore, a Simon cipher implementation is denoted as Simon2n/nm. For example, Simon64/128 refers to the cipher operating on a 64-bit plaintext block (n=32) that uses a 128-bit key.[1] The block component of the cipher is uniform between the Simon implementations; however, the key generation logic is dependent on the implementation of 2, 3 or 4 keys.
Simon supports the following combinations of block sizes, key sizes and number of rounds:[1]
| Block size (bits) | Key size (bits) | Rounds |
|---|---|---|
| 32 | 64 | 32 |
| 48 | 72 | 36 |
| 96 | 36 | |
| 64 | 96 | 42 |
| 128 | 44 | |
| 96 | 96 | 52 |
| 144 | 54 | |
| 128 | 128 | 68 |
| 192 | 69 | |
| 256 | 72 |
Description of the Key Schedule
Let notate a left circular shift by bits.
The key schedule is mathematically described as
The key schedule structure may or may not be balanced. The key word count of is used to determine the structure of the key expansion, resulting in a total bit width of . The key word expansion consists of a right shift, XOR and a constant sequence, . The bit operates on the lowest bit of the key word once per round[7].
Description of the Constant Sequence
The constant sequence, , is created by a Linear Feedback Shift Register (LFSR). The logical sequence of bit constants is set by the value of the key and block sizes. The LFSR is created by a 5-bit field. The constant bit operates on a key block once per round on the lowest bit in order to add non-key-dependent entropy to the key schedule. The LFSR has different logic for each sequence; however, the initial condition is the same for encryption. The initial condition of the LFSR for decryption varies on the round.
| Constant Sequence |
|---|
Opposition to ISO approval
Expert delegates to the International Organization for Standardization from several countries including Germany, Japan and Israel have opposed the efforts by the NSA to standardise the Simon and Speck ciphers, citing concerns that the NSA is pushing for their standardisation with knowledge of exploitable weaknesses in the ciphers, based on partial evidence of weaknesses in the ciphers, lack of clear need for standardisation of the new ciphers, and the NSA's previous involvement in the creation and promotion of the backdoored Dual_EC_DRBG cryptographic algorithm.[9]
Simon has been severely criticized and ISO standardization has been rejected.[10]
See also
References
- 1 2 3 4 The Simon and Speck Families Of Lightweight Block Ciphers (PDF). ePrint. Retrieved 2016-06-16.
- ↑ "Differential and Linear Cryptanalysis of Reduced-Round Simon". Retrieved 2014-04-16.
- ↑ Farzaneh Abed, Eik List, Stefan Lucks, Jakob Wenzel (5 March 2014). Differential Cryptanalysis of Round-Reduced Simon and Speck (PDF). FSE 2014. conference slides.
- ↑ Hoda Alkhzaimi, Martin Lauridsen (28 Aug 2013). "Cryptanalysis of the SIMON Family of Block Ciphers" (PDF).
- ↑ Schneier, Bruce. "SIMON and SPECK: New NSA Encryption Algorithms". Schneier on Security. Retrieved 2013-07-17.
- ↑ Claire Swedberg (17 July 2015). "NSA Offers Block Ciphers to Help Secure RFID Transmissions". RFID Journal.
- 1 2 Brian Degnan and Gregory Durgin (10 November 2017). "Simontool: Simulation Support for the Simon Cipher". Lay summary.
- ↑ "We need to talk about mathematical backdoors in encryption algorithms". Retrieved 2018-08-06.
- ↑ "Distrustful U.S. allies force spy agency to back down in encryption fight".
- ↑ Insights an reasons why Speck and Simon have been rejected from ISO standardization