Shamoon
Shamoon,[lower-alpha 1] also known as W32.DisTrack,[1] is a modular computer virus discovered by Seculert[2] in 2012, targeting recent 32-bit NT kernel versions of Microsoft Windows. The virus has been noted to have behavior differing from other malware attacks, due to the destructive nature and the cost of the attack and recovery. Known years later as the "biggest hack in history,"[3] the virus was apparently intended for cyber warfare.[4] Shamoon can spread from an infected machine to other computers on the network. Once a system is infected, the virus continues to compile a list of files from specific locations on the system, upload them to the attacker, and erase them. Finally the virus overwrites the master boot record of the infected computer, making it unusable.[5][3] The virus has been used for cyber warfare against the national oil companies of Saudi Arabia's Saudi Aramco and Qatar's RasGas.[6][5][7] Its discovery was announced on 16 August 2012 by Symantec,[5] Kaspersky Lab,[8] and Seculert.[9] Similarities have been highlighted by Kaspersky Lab and Seculert between Shamoon and the Flame malware.[8][9]
Before the attack
The malware was unique, used to target the Saudi government by causing destruction to the state owned national oil company Saudi Aramco. The attackers posted a pastie on PasteBin.com hours prior to the wiper logic bomb occurring, citing oppression and the Al-Saud regime as a reason behind the attack.[10] The attack was well-staged, according to Christina Kubecka, a former security advisor to Saudi Aramco after the attack and group leader of security for Aramco Overseas.[3] An unnamed Saudi Aramco employee on the Information Technology team opened a malicious phishing email, allowing initial entry into the computer network around mid-2012.[11]
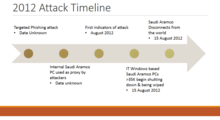
Kubecka also detailed in her Black Hat USA talk Saudi Aramco placed the majority of their security budget on the ICS control network, leaving the business network at risk for a major incident. "When you realize most of your security budget was spent on ICS & IT gets Pwnd".[11]
Attacker announcement
"We, behalf of an anti-oppression hacker group that have been fed up of crimes and atrocities taking place in various countries around the world, especially in the neighboring countries such as Syria, Bahrain, Yemen, Lebanon, Egypt and ..., and also of dual approach of the world community to these nations, want to hit the main supporters of these disasters by this action. One of the main supporters of this disasters is Al-Saud corrupt regime that sponsors such oppressive measures by using Muslims oil resources. Al-Saud is a partner in committing these crimes. It's hands are infected with the blood of innocent children and people. In the first step, an action was performed against Aramco company, as the largest financial source for Al-Saud regime. In this step, we penetrated a system of Aramco company by using the hacked systems in several countries and then sended a malicious virus to destroy thirty thousand computers networked in this company. The destruction operations began on Wednesday, Aug 15, 2012 at 11:08 AM (Local time in Saudi Arabia) and will be completed within a few hours."
During the attack
The Shamoon attack was designed to do two things, replace the data on hard drives with an image of a burning American Flag and report the addresses of infected computers back to the computer inside the company’s network. The virus consisted of three components, the Dropper, the Wiper and the Reporter. The Dropper is the main component and the source of the infection. This component drops the Wiper and the Reporter onto the infected computer, copies itself to network shares, executes itself and creates a service to start itself whenever Windows starts.[12] The Wiper was the destructive component. This component gathers all the files from locations of the infected computers and erases them. It then sends information about the files to the attacker and the erased files are overwritten with corrupted files so they cannot be recovered. The Reporter component sends the infected information back to the attacker.
On 15 August 2012 at 11:08 am local time, over 30,000 Windows based systems began to be overwritten. Symantec found some of the affected systems had the image of an American flag whilst data was being deleted and overwritten.[5] Saudi Aramco announced the attack on their Facebook page and went offline again until a company statement was issued on 25 August 2012. The statement falsely reported normal business was resumed on 25 August 2012. However a Middle Eastern journalist leaked photographs taken on 1 September 2012 showing kilometers of petrol trucks unable to be loaded due to backed business systems still inoperable.

"Saudi Aramco has restored all its main internal network services that were impacted on August 15, 2012, by a malicious virus that originated from external sources and affected about 30,000 workstations. The workstations have since been cleaned and restored to service. As a precaution, remote Internet access to online resources was restricted. Saudi Aramco employees returned to work August 25, 2012, following the Eid holidays, resuming normal business. The company confirmed that its primary enterprise systems of hydrocarbon exploration and production were unaffected as they operate on isolated network systems. Production plants were also fully operational as these control systems are also isolated."
On August 29, 2012 the same attackers behind Shamoon posted another pastie on PasteBin.com, taunting Saudi Aramco with proof they still retained access to the company network. The post contained the username and password on security and network equipment and the new password for Aramco CEO Khalid Al-Falih[13] The attackers also referenced a portion of the Shamoon malware as further proof in the pastie:
- "mon 29th aug, good day, SHN/AMOO/lib/pr/~/reversed
- We think it's funny and weird that there are no news coming out from Saudi Aramco regarding Saturday's night. well, we expect that but just to make it more clear and prove that we're done with we promised, just read the following facts -valuable ones- about the company's systems:
- internet service routers are three and their info as follows: Core router: SA-AR-CO-1# password (telnet): c1sc0p@ss-ar-cr-tl / (enable): c1sc0p@ss-ar-cr-bl Backup router: SA-AR-CO-3# password (telnet): c1sc0p@ss-ar-bk-tl / (enable): c1sc0p@ss-ar-bk-bl Middle router: SA-AR-CO-2# password (telnet): c1sc0p@ss-ar-st-tl / (enable): c1sc0p@ss-ar-st-bl
- Khalid A. Al-Falih, CEO, email info as follows: Khalid.falih@aramco.com password:kal@ram@sa1960
- security appliances used:
- Cisco ASA # McAfee # FireEye :
- default passwords for all!!!!!!!!!!
- We think and truly believe that our mission is done and we need no more time to waste. I guess it's time for SA to yell and release something to the public. however, silence is no solution.
- I hope you enjoyed that. and wait our final paste regarding SHN/AMOO/lib/pr/~
- angry internet lovers #SH"
According to Kubecka, in order to restore operations, Saudi Aramco used its large private fleet of aircraft and available funds to purchase much of the world's hard drives, driving the price up. New hard drives were required as quickly as possible so oil prices were not affected by speculation. By September 1, 2012 gasoline resources were dwindling for the public of Saudi Arabia 17 days after the August 15th attack. RasGas was also affected by a different variant, crippling them in a similar manner.[11]
It is unclear why the attacker may have an interest in actually destroying the infected PC. Kaspersky Labs hinted that the 900 KB malware could be related to Wiper, that was used in a cyber attack on Iran in April. After a 2-day analysis, the company erroneously concluded that the malware is more likely to come from "scriptkiddies" who were inspired by Wiper.[14] Later, in a blog post, Eugene Kaspersky clarified the use of Shamoon categorizing as cyber warfare.[15]
The virus has hit companies within the oil and energy sectors.[6][7] A group named "Cutting Sword of Justice" claimed responsibility for an attack on 35,000 Saudi Aramco workstations, causing the company to spend a week restoring their services.[16] The group later indicated that the Shamoon virus had been used in the attack.[17] Computer systems at RasGas were also knocked offline by an unidentified computer virus, with some security experts attributing the damage to Shamoon.[18]
Shamoon made a surprise comeback in November 2016 according to Symantec,[19] and it was involved in a new attack on 23 January 2017.[20]
Payload
The malware had a logic bomb which triggered the master boot record and data wiping payload at 11:08 am local time on Wednesday, August, 15. The attack occurred during the month of Ramadan in 2012. It would appear that the attack was timed to occur after most staff had gone on holiday reducing the chance of discovery before maximum damage could be caused, hampering recovery.
Shamoon uses a number of components to infect computers. The first component is a dropper, which creates a service with the name ‘NtsSrv’ to remain persistent on the infected computer. It spreads across a local network by copying itself on to other computers and will drop additional components to infected computers. The dropper comes in 32-bit and 64-bit versions. If the 32-bit dropper detects a 64-bit architecture, it will drop the 64-bit version. The malware also contains a disk wiping component, which utilizes an Eldos-produced driver known as RawDisk to achieve direct user-mode access to a hard drive without using Windows APIs. The component overwrites files with portions of an image; the 2012 attack used an image of a burning U.S. flag, while the 2016 attack used a photo of the body of Alan Kurdi.[21][22][19]
Notes
- ↑ "Shamoon" is part of a directory string found in the virus' Wiper component.
References
- ↑ "Joint Security Awareness Report (JSAR-12-241-01B):'Shamoon/DistTrack' Malware (Update B)". United States Department of Homeland Security ICS-CERT. 2017-04-18. Retrieved 2017-11-03.
- ↑ Darpana Kutty (2012-08-18). "Seculert: 'Shamoon' malware covers its tracks by crippling infected systems after stealing data". topnews.in. TopNews Network. Retrieved 2014-03-25.
- 1 2 3 Jose Pagliery (2015-08-05). "The inside story of the biggest hack in history". Retrieved 2012-08-19.
- ↑ Iain Thompson (2012-08-17). "Exhibitionist Shamoon virus blows PCs' minds". The Register. Retrieved 2017-11-03.
- 1 2 3 4 Symantec Security Response (2012-08-16). "The Shamoon Attacks". Symantec. Retrieved 2012-08-19.
- 1 2 Tim Sandle (2012-08-18). "Shamoon virus attacks Saudi oil company". Digital Journal. Retrieved 2012-08-19.
- 1 2 "Shamoon virus targets energy sector infrastructure". BBC News. 2012-08-17. Retrieved 2012-08-19.
- 1 2 GReAT (2012-08-16). "Shamoon the Wiper — Copycats at Work". Archived from the original on 2012-08-20. Retrieved 2012-08-19.
- 1 2 Seculert (2012-08-16). "Shamoon, a two-stage targeted attack". Seculert. Archived from the original on 2012-08-20. Retrieved 2012-08-19.
- ↑ Cutting Sword of Justice (2012-08-15). "Pastie:'Untitled'". Retrieved 2017-11-03.
- 1 2 3 Christina Kubecka (2015-08-03). "How to Implement IT Security after a Cyber Meltdown". Retrieved 2017-11-03. (PDF slides, YouTube video)
- ↑ Mackenzie, Heather (2012-10-25). "Shamoon Malware and SCADA Security – What are the Impacts?".
- ↑ "Saudi Aramco hug, another one". 2012-08-29. Retrieved 2017-11-03.
- ↑ Wolfgang Gruener (2012-08-18). "Cyber Attack: Shamoon Malware Infects, Steals, Wipes MBR". Tom's Hardware. Retrieved 2017-03-22.
- ↑ Eugene Kaspersky (2017-03-06). "StoneDrill: We've Found New Powerful "Shamoon-ish" Wiper Malware – and It's Serious". Retrieved 2017-11-03.
- ↑ Nicole Perlroth (2012-10-23). "Cyberattack On Saudi Firm Disquiets U.S." The New York Times. pp. A1. Retrieved 2012-10-24.
- ↑ Elinor Mills (2012-08-30). "Virus knocks out computers at Qatari gas firm RasGas". CNET. Retrieved 2012-09-01.
- ↑ "Computer virus hits second energy firm". BBC News. 2012-08-31. Retrieved 2012-09-01.
- 1 2 Symantec Security Response (2016-11-30). "Shamoon: Back from the dead and destructive as ever". Symantec. Retrieved 2016-12-06.
- ↑ Reuters Staff (2017-01-23). "Saudi Arabia warns on cyber defense as Shamoon resurfaces". Reuters. Retrieved 2017-01-26.
- ↑ Sean Gallagher (2016-12-01). "Shamoon wiper malware returns with a vengeance". Ars Technica. Retrieved 2017-07-03.
- ↑ Nicole Perlroth (2012-08-24). "Among Digital Crumbs from Saudi Aramco Cyberattack, Image of Burning U.S. Flag". Bits. The New York Times. Retrieved 2017-07-03.