Data center security
Data center security is the set of policies, precautions and practices adopted to avoid unauthorized access and manipulation of a data center's resources. The data center houses the enterprise applications and data, hence why providing a proper security system is critical. Denial of service (DoS), theft of confidential information, data alteration, and data loss are some of the common security problems afflicting data center environments.[1]
The need for a secure data center
The number of reported security attacks, including those affecting Data Centers continues to grow year by year. Attacks and attack tools are becoming more and more sophisticated. On one hand, the expansion of the Internet and the growing complexity of protocols and applications used in Data Centers result in an increasing number of exploitable vulnerabilities. On the other hand, hackers use the openness of the Internet to communicate and develop automated tools that facilitate the identification and exploitation of those vulnerabilities. Attacks are usually also initiated by internal trusted personnel.[2] In fact, studies show that internal attacks tend to be more damaging because of the variety and amount of information available inside organizations.
The cost of a breach of security can have some devastating consequence both on the company managing the data center and on the customers whose data were a breach. For example, the 2012 breach at Global Payments, a processing vendor for Visa, where 1.5 millions of credit card numbers were stolen, highlights the risks of storing and managing valuable and confidential data.[3] As a result, Global Payments partnership with Visa was terminated and, it was estimated that they lost over $100 million. The consequences of permitting such data breaches can be damaging to an organization of any size. Besides a huge financial loss, the company is affected by data breaches may lose the confidence of their business partners and their customers who provided their data to the breached company.
According to the Cost of a Data Breach Survey,[4] in which 49 U.S. companies in 14 different industry sectors participated, they noticed that:
- 39% of companies say negligence was the primary cause of data breaches
- Malicious or criminal attacks account for 37 percent of total breaches.
- The average cost of a breach is $5.5 million.
We realized that negligent and malicious are the main causes of data breach, which is why companies are supposed to take steps to minimize the risks of an attack. Companies belonging to a certain industry such as healthcare, technology, finances, are taking care of large amounts of extremely sensitive data, such as medical records, credit card numbers, social security numbers. Those type companies must be extremely vigilant in order to protect their clients’ data.[4]
As time passes, people always find inventive ways to bypass the security measures put in place by data centers. Every business related to data centers will have to overcome those challenges and prioritize data center security. The amount of data passed in those data center will only grow year after year via cloud-computing and phones, ergo those responsible to secure that valuable information much assess their risk which includes physical breaches.[4]
Vulnerabilities and common attacks
Threats
The following are some of the most common threats to Data Centers:
- DoS (Denial of Service)
- Breach of confidential information
- Data theft or alteration
- Unauthorized use of computing resources
- Identity theft
Vulnerabilities
Common vulnerabilities in data centers are related to the following areas:
- Implementation: Software and protocols flaws, wrong software design or incomplete testing, etc.
- Configuration: Use of defaults, elements not properly configured, etc.
- Design: Ineffective or inadequate security design, lack of or inappropriate implementation of redundancy mechanisms, etc.
Exploitation of out-of-date software
Most attacks on data centers exploit well-known vulnerabilities that are usually discovered an announced months before the first attack takes place. The worms CodeRed,[5] Nimda,[6] and SQL Slammer[7] are examples of exploiting known vulnerabilities that could have been avoided. This clearly indicates that a significant number of exploits on the Internet by using the latest releases of software.
Exploitation of software defaults
Many systems are shipped with default accounts and passwords, which are exploited for unauthorized access and theft of information, among other threats.
Common attacks
Common attacks include:
- Scanning or Probing:
A probe is an attack which is deliberately crafted so that its target detects and reports it with a recognizable “fingerprint” in the report. The attacker then uses the collaborative infrastructure to learn the detector’s location and defensive capabilities from this report.[8] this is more like a reconnaissance activity because it precedes an attack and it's goal is to gain access by discovering information about a system or network.
- DoS (Denial of service):
A denial-of-service attack occurs when legitimate users are unable to access information systems, devices, or other network resources due to the actions of a malicious cyber threat actor.[9] This type of attack can take different forms like for example generating large volume of data to deliberately consume limited resources as bandwidth, CPU cycles, and memory blocks.
- Distributed Denial of Service (DDoS):
This kind of attack is a particular case of DoS where a large number of systems are compromised and used as source or traffic on a synchronized attack. In this kind of attack, the hacker does not use only one IP address but thousand of them.[10]
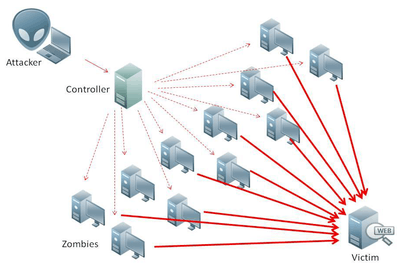
- Unauthorized Access:
When someone other than an account owner uses privileges associated to a compromised account to access to restricted resources using a valid account or a backdoor.[11]
- Eavesdropping:
Etymologically, Eavesdropping means Secretly listen to a conversation.[12] In the wetworking filed, it is an unauthorized interception of information (usernames, passwords) that travels on the network. The most common cases of eavesdropping in Data Centers include intercepting typical and critical user transactions such as logon sessions.
- Viruses and Worms:
They are both malicious code that produces once executed undesired results on the infected system. The malicious code usually remains in the system until the damage is discovered. The difference between viruses and worms is that, worms are self-replicating malwares that propagate without human intervention[13] while viruses are also self-replicating but they need some kind of human action to infect the system.[14]
- Internet Infrastructure Attacks:
This kind of attack targets the critical components of the Internet infrastructure rather than individual systems or networks.
- Trust Exploitation:
These attacks exploit the trust relationships that computer systems have to communicate.
- Session Hijacking also known as cookie hijacking:
Consists of stealing a legitimate session established between a target and a trusted host. The attacker intercepts the session and makes the target believe it is communicating with the trusted host.[15]
- Buffer Overflow Attacks:
This kind of attack occurs when a program allocates memory buffer space beyond what it had reserved; it results in memory corruption affecting the data stored in the memory areas that were overflowed.[16]
- Layer 2 Attacks:
This type of attack exploit the vulnerabilities of data link layer protocols and their implementations on layer 2 switching platforms.
Network Security Infrastructure
The network security infrastructure includes the security tools used in Data Center to enforce security policies. The tools include packet-filtering technologies such as ACLs, firewalls and intrusion detection systems (IDSs) both network-based and host-based.
ACLs (Access Control List)
ACLs are filtering mechanisms explicitly defined based on packet header information to permit or deny traffic on specific interfaces. Generally, an ACL is set up as a list that is applied sequentially on the packets until a match is found. Once the match is found, the associated permit or deny operation is applied. ACLs are used in multiple locations within the Data Center such as the Internet Edge and the intranet server farm. The following describes standard and extended access lists:
Standard ACLs: the simplest type of ACL filtering traffic solely based on source IP addresses. Standard ACLs are typically deployed to control access to network devices for network management or remote access. For example, you can configure a standard ACL in a router to specify which systems are allowed to Telnet to it. Standard ACLs aren't recommended option for traffic filtering due to their lack of granularity. Standard ACLSs are configured with a number between 1 and 99 in Cisco routers.
Extended ACLs: Extended ACL filtering decisions can be based on source and destination IP addresses, Lyaer 4 protocol, Layer 4 ports, ICMP message type and code, type of service, and precedence. In Cisco routers, you can define extended ACLs by name or by a number in the 100 to 199 range.[1]
Firewalls
A firewall is a sophisticated filtering device that separates LAN segments, giving each segment a different security level and establishing a security perimeter that controls the traffic flow between segments.Firewalls are most commonly deployed at the Internet Edge where they act as boundary to the internal networks.They are expected to have the following characteristics:
Performance: the main goal of a firewall is to separate the secured and the unsecured areas of a network. Firewalls are then post in the primary traffic path potentially exposed to large volumes of data. Hence, performance becomes a natural design factor to ensure that the firewall meets the particular requirements.
Application support: Another important aspect is the ability of a firewall to control and protect a particular application or protocol, such as Telnet, FTP, and HTTP. The firewall is expected to understand application-level packet exchanges to determine whether packets do follow the application behavior and, if they do not, do deny the traffic.
There are different types of firewalls based on their packet-processing capabilities and their awareness of application-level information:
- Packet-filtering firewalls
- Proxy firewalls
- Stateful firewalls
- Hybrid firewalls[1]
IDSs
IDSs are real-time systems that can detect intruders and suspicious activities and report them to a monitoring system. They are configured to block or mitigate intrusions in progress and eventually immunize the systems from future attacks. They have two fundamental components:
- Sensors: Appliances and software agents that analyze the traffic on the network or the resource usage on end systems to identify intrusions and suspicious activities.
- IDS management: Single- or multi-device system used to configure and administer sensors and to additionally collect all the alarm information generated by the sensors. The sensors are equivalent to surveillance tools, and IDS management is the control center watching the information produced by the surveillance tools.[1]
Layer 2 security
Cisco Layer 2 switches provide tools to prevent the common Layer 2 attacks (Scanning or Probing, DoS, DDoS, etc.). The following are some security features covered by the Layer 2 Security:
- Port Security
- ARP Inspection
- Private VLANs
- Private VLANs and Firewalls
Data Center security measures
The process of securing a Data Center requires both a comprehensive system-analysis approach and an ongoing process that improves the security levels as the Data Center evolves. The Data Center is constantly evolving as new applications or services become available. Attacks are becoming more sophisticated and more frequent. These trends require a steady evaluation of security readiness.
A key component of the security-readiness evaluation is the policies that govern the application of security in the network including the Data Center. The application includes both the design best practices and the implementation details.[1] As a result, security is often considered as a key component of the main infrastructure requirement. Since a key responsibility of the data centers is to make sure of the availability of the services, data center management systems often consider how its security affects traffic flows, failures, and scalability. Due to the fact that security measures may vary depending on the data center design, the use of unique features, compliance requirements or the company's business goals, there isn't a set of specific measures that cover all possible scenarios.[17]
There exist in general two types of data center security: the Physical Security and the Virtual Security.[18]
Physical Security
The physical security of a data center is the set of protocol built-in within the data center facilities in order to prevent any physical damage to the machines storing the data. Those protocols should be able to handle everything ranging from natural disasters to corporate espionage to terrorist attacks.[19]
The result of a physical attack on a data center could possibly cause data racks being damaged, destroyed or stolen, which means that the data it contains might have been lost or inaccessible. Planning in advanced and putting the right and modern security measures in place can drastically reduce the risks of a physical attack on a data center. For instance, to reduce the risks of leaks caused by workers, it is a good practice to make sure that the employees' backgrounds are well checked, and that nontechnical personnel is not allowed to work with data servers and repositories unless they receive adequate training. Additionally, the security team in place should effectively know what to do using a disaster or a treat to the security of the data center.
To prevent physical attacks, data centers use techniques such as:
- Anti-tailgating/Anti-pass-back turnstile gate. Only permits one person to pass through after authentication.
- Single entry point into co-location facility.
- Three-factor authentication
- Further access restriction to private cages
- SSAE 16 compliant facilities.
- On-site security
- CCTV security network
- locations and access points with 90-day video retention.[20]
- Checking the provenance and design of hardware in use
- Reducing insider risk by monitoring activities and keeping their credentials safe[21]
- Minimization of traffic through dedicated data halls, suites, and cages.
- Monitoring of Temperature and humidity
- Fire prevention with zoned dry-pipe sprinkler
- 24×7 on-site security guards, NOC Services and technical team
- 24x7 on-site NOC services
- Natural disaster risk-free locations[22]
Virtual Security
Virtual security is security measures put in place by the data centers to prevent remote unauthorized access that will affect the integrity, availability or confidentiality of data stored on servers.[23]
Virtual or network security is a hard task to handle as there exist many ways it could be attacked. The worst part of it is that it is evolving years after years. For instance, an attacker could decide to use a malware (or similar exploits) in order to bypass the various firewalls to access the data. Old systems may as well put security at risk as they do not contain modern methods of data security.[18]
Virtual attacks can be prevented with techniques such as
- Heavy data encryption during transfer or not: 256-bit SSL encryption for web applications.1024-bit RSA public keys for data transfers. AES 256-bit encryption for files and databases.
- Logs auditing activities of all users.
- Secured usernames and passwords: Encrypted via 256-bit SSL, requirements for complex passwords, set up of scheduled expirations, prevention of password reuse.
- Access based on the level of clearance.
- AD/LDAP integration.
- Control based on IP addresses.
- Encryption of session ID cookies in order to identify each unique user.
- Two-factor authentication availability.
- Third party penetration testing performed annually[20]
- Malware prevention through firewalls and automated scanner[24]
References
- 1 2 3 4 5 Maurizio Portolani, Mauricio Arregoces(2004). Data Center Fundamentals. Publishers, Cisco Press, 800 East 96th Street Indianapolis, IN 46240 USA, Chap.5
- ↑ 2003 CSI/FBI report "Computer Crime and Security Survey."
- ↑ Jessica Silver-Greenberg After a Data Breach, Visa Removes a Service Provider
- 1 2 3 The Four Layers of Data Center Physical Security for a comprehensive and integrated Approach
- ↑ Moore, David; Colleen Shannon (c. 2001). "The Spread of the Code-Red Worm (CRv2)". CAIDA Analysis. Retrieved 2006-10-03.
- ↑ "Net-Worm: W32/Nimda Description | F-Secure Labs". F-secure.com
- ↑ Leyden, John (6 February 2003). "Slammer: Why security benefits from proof of concept code".
- ↑ "Security Against Probe-Response Attacks in Collaborative Intrusion Detection" Vitaly Shmatikov and Ming-Hsiu Wang The University of Texas at Austin
- ↑ "Understanding Denial-of-Service Attacks". US-CERT. 6 February 2013. Retrieved 26 May 2016.
- ↑ Khalifeh,, Soltanian, Mohammad Reza. Theoretical and experimental methods for defending against DDoS attacks. Amiri, Iraj Sadegh, 1977-. Waltham, MA. ISBN 0128053992. OCLC 930795667.
- ↑ GIAC Certifications. Global Information Assurance Certification Paper.
- ↑ "eavesdrop - Definition of eavesdrop in English by Oxford Dictionaries". Oxford Dictionaries - English.
- ↑ Barwise, Mike. "What is an internet worm?". BBC.
- ↑ Stallings, William (2012). Computer security : principles and practice. Boston: Pearson. p. 182. ISBN 978-0-13-277506-9.
- ↑ "Warning of webmail wi-fi hijack". BBC News. August 3, 2007.
- ↑ ""Modern Overflow Targets"" (PDF).
- ↑ Cisco SAFE Reference Guide chap.4
- 1 2 Rich Banta Types of Data Center Security
- ↑ Sara D. Scalet 19 ways to build physical security into your data center
- 1 2 Security and Data Center Overview
- ↑ Google Infrastructure Security Design Overview
- ↑ iliad Data Center['http://www.iliad-datacenter.com/pdf/iliad-dc-security.pdf' 'Data Center Security'] chap.4
- ↑ Securing Microsoft's Cloud Infrastructure 2009.
- ↑ Data Centre Management