Bluejacking

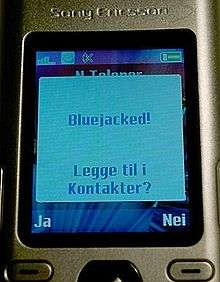
Bluejacking is the sending of unsolicited messages over Bluetooth to Bluetooth-enabled devices such as mobile phones, PDAs or laptop computers, sending a vCard which typically contains a message in the name field (i.e., for bluedating or bluechat) to another Bluetooth-enabled device via the OBEX protocol.
Bluetooth has a very limited range, usually around 10 metres (32.8 ft) on mobile phones, but laptops can reach up to 100 metres (328 ft) with powerful (Class 1) transmitters.
Origins
Bluejacking was reportedly first carried out between 2001 and 2003 by a Malaysian IT consultant who used his phone to advertise Sony Ericsson to a single Nokia 7650 phone in a Malaysian bank. He also invented the name, which he claims is an amalgam of Bluetooth and ajack, his username on Esato, a Sony Ericsson fan online forum. Jacking is, however, an extremely common shortening of "hijack', the act of taking over something.[1][2] Ajack's original posts are hard to find, but references to the exploit are common in 2003 posts.
Another user on the forum claims earlier discovery,[3] reporting a near-identical story to that attributed to Ajack, except he/she describes bluejacking 44 Nokia 7650 phones instead of one, and the location is a garage, seemingly in Denmark, rather than a Malaysian Bank. Also, the message was an insult to Nokia owners rather than a Sony Ericsson advertisement.
Usage
Bluejacking is usually harmless, but because bluejacked people generally don't know what has happened, they may think that their phone is malfunctioning. Usually, a bluejacker will only send a text message, but with modern phones it's possible to send images or sounds as well. Bluejacking has been used in guerrilla marketing campaigns to promote advergames.
Bluejacking is also confused with Bluesnarfing, which is the way in which mobile phones are illegally hacked via Bluetooth.
Fictional reference in Person of Interest
The authentic bluejacking as described here is not the same exploit which was frequently depicted in the Person of Interest television series; that fictional exploit portrayed different and more invasive capabilities.