Let's Encrypt
Let's Encrypt is a non-profit certificate authority run by Internet Security Research Group (ISRG) that provides X.509 certificates for Transport Layer Security (TLS) encryption at no charge. The certificate is valid for 90 days, during which renewal can take place at any time. The offer is accompanied by an automated process designed to overcome manual creation, validation, signing, installation, and renewal of certificates for secure websites.[2][3] It launched on April 12, 2016.[4][5]
 | |
| Formation | November 18, 2014 |
|---|---|
| Founder | |
| Headquarters | San Francisco, California, U.S. |
| Coordinates | 37.800322°N 122.449951°W |
| Services | X.509 certificate authority |
Parent organization | Internet Security Research Group |
Budget (2019) | US$3.6 million[1] |
Staff (2019) | 13 |
| Website | letsencrypt |
The project claims its goal is to make encrypted connections to World Wide Web servers ubiquitous.[6] By eliminating payment, web server configuration, validation email management and certificate renewal tasks, it is meant to significantly lower the complexity of setting up and maintaining TLS encryption.[7] On a Linux web server, execution of only two commands is sufficient to set up HTTPS encryption and acquire and install certificates.[8][9]
To that end, a software package was included into the official Debian and Ubuntu software repositories.[10][11] Current initiatives of major browser developers such as Mozilla and Google to deprecate unencrypted HTTP are counting on the availability of Let's Encrypt.[12][13] The project is acknowledged to have the potential to accomplish encrypted connections as the default case for the entire Web.[14]
The service only issues domain-validated certificates, since they can be fully automated. Organization Validation and Extended Validation Certificates both require human validation of any registrants, and are therefore not offered by Let's Encrypt.[15] The domain validation (DV) utilized by Let's Encrypt dates back to 2002 and was at first controversial when introduced by GeoTrust before becoming a widely accepted method for the issuance of SSL certificates [16]
By being as transparent as possible, they hope to both protect their own trustworthiness and guard against attacks and manipulation attempts. For that purpose they regularly publish transparency reports,[17] publicly log all ACME transactions (e.g. by using Certificate Transparency), and use open standards and free software as much as possible.[8]
Support of ACME v2 and wildcard certificates was added in March 2018.[18]
Involved parties
Let's Encrypt is a service provided by the Internet Security Research Group (ISRG), a public benefit organization. Major sponsors are the Electronic Frontier Foundation (EFF), the Mozilla Foundation, OVH, Cisco Systems, Facebook, Google Chrome, and Internet Society. Other partners include the certificate authority IdenTrust, the University of Michigan (U-M), the Stanford Law School, and the Linux Foundation,[19] as well as Stephen Kent from Raytheon/BBN Technologies and Alex Polvi from CoreOS.[8]
Board members (as of March 2020)[20]
- Josh Aas (ISRG) — ISRG Executive Director
- Richard Barnes (Cisco)
- Jennifer Granick (ACLU)
- Aanchal Gupta (Facebook)
- J. Alex Halderman (University of Michigan)
- Max Hunter (EFF)
- Pascal Jaillon (OVH)
- Christine Runnegar (Internet Society)
Technical Advisory Board[20]
- Rich Salz (Akamai Technologies)
- Joe Hildebrand (Independent, formerly Mozilla Corporation, formerly Cisco Systems at funding time)
- Jacob Hoffman-Andrews (Electronic Frontier Foundation)
- J. C. Jones (Mozilla Foundation)
- Russ Housley (Independent)
- Ryan Hurst (Google)
- Stephen Kent (Independent)
- Karen O'Donoghue (Internet Society)
- Ivan Ristic (Independent)
- Yueting Lee (Facebook)
Technology
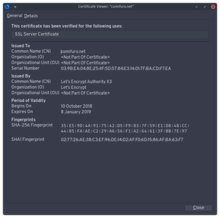
In June 2015, Let's Encrypt announced the generation of their first RSA root certificate, ISRG Root X1.[21] The root certificate was used to sign two intermediate certificates,[21] which are also cross-signed by the certificate authority IdenTrust.[22][23] One of the intermediate certificates is used to sign issued certificates, while the other is kept offline as a backup in case of problems with the first intermediate certificate.[21] Because the IdenTrust certificate is preinstalled in major Web browsers, Let's Encrypt certificates can normally be validated and are accepted upon installation[24] even before browser vendors include the ISRG root certificate as a trust anchor.
The Let's Encrypt developers planned to generate an ECDSA root certificate as well later in 2015,[21] which was pushed back to early 2016, then to 2019, and is still not available as of May 1, 2020.[25][26][27]
ACME protocol
The challenge–response protocol used to automate enrolling with the certificate authority is called Automated Certificate Management Environment (ACME). It involves various requests to the Web server on the domain that is covered by the certificate. Based on whether the resulting responses match the expectations, control of the enrollee over the domain is assured (domain validation). In order to do that, the ACME client software sets up a special TLS server on the server system that gets queried by the ACME certificate authority server with special requests using Server Name Indication (Domain Validation using Server Name Indication, DVSNI).
The validation processes are run multiple times over separate network paths. Checking DNS entries is provisioned to be done from multiple geographically diverse locations to make DNS spoofing attacks harder to do.
ACME interactions are based on exchanging JSON documents over HTTPS connections.[28] A draft specification is available on GitHub,[29] and a version has been submitted to the Internet Engineering Task Force (IETF) as a proposal for an Internet standard.[30]
Let's Encrypt implemented its own draft of the ACME protocol. At the same time, they pushed for standardization. This led to a "proposed standard" (RFC8555) in May 2019. It introduced breaking changes and as such it has been dubbed ACMEv2. Let's Encrypt implemented the new version and started pushing existing clients into upgrades. The nudging was implemented with intermittent down-times of the ACMEv1 API. The end-of-lifetime was announced with dates and phases in "End of Life Plan for ACMEv1".[31]
ACMEv1 end of life
New account registrations
Staging environment:
- 2019 – August 6 to August 7 – 1st brownout
- 2019 – August 13 to August 15 – 2nd brownout
- 2019 – August 27 to September 3 – 3rd brownout
- 2019 – October 1 – new ACME v1 account registrations permanently disabled
Production environment:
- 2019 – October 10 to October 11 – 1st brownout
- 2019 – October 16 to October 18 – 2nd brownout
- 2019 – November 8 – new ACME v1 account registration permanently disabled
New domain validation
2020 June – new domain validations will be disabled
Certificate renewal validations
24-hour brownouts will start in January 2021
2021 June – ACMEv1 will be completely disabled
Software implementation
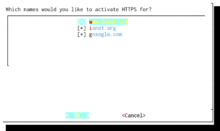
The certificate authority consists of a piece of software called Boulder, written in Go, that implements the server side of the ACME protocol. It is published as free software with source code under the terms of version 2 of the Mozilla Public License (MPL).[32] It provides a RESTful API that can be accessed over a TLS-encrypted channel. Boulder uses cfssl, a CloudFlare PKI/TLS toolkit, internally.[33]
An Apache-licensed[34] Python certificate management program called certbot (formerly letsencrypt) gets installed on the client side (the Web server of an enrollee). This is used to order the certificate, to conduct the domain validation process, to install the certificate, to configure the HTTPS encryption in the HTTP server, and later to regularly renew the certificate.[8][35] After installation and agreeing to the user license, executing a single command is enough to get a valid certificate installed. Additional options like OCSP stapling or HTTP Strict Transport Security (HSTS) can also be enabled.[28] Automatic setup initially only works with Apache and nginx.
Let's Encrypt issues certificates valid for 90 days. The reason given is that these certificates "limit damage from key compromise and mis-issuance" and encourage automation.[36]
Initially, Let's Encrypt developed its own ACME client - Certbot - as an official implementation. This has been transferred to Electronic Frontier Foundation and its name "letsencrypt" has been changed to "certbot". There is a large selection of ACME Clients and Projects for a number of environments developed by the community.[37]
History
The Let's Encrypt project was started in 2012 by two Mozilla employees, Josh Aas and Eric Rescorla, together with Peter Eckersley at the Electronic Frontier Foundation and J. Alex Halderman at the University of Michigan. Internet Security Research Group, the company behind Let's Encrypt, was incorporated in May 2013.[38]
Let's Encrypt was announced publicly on November 18, 2014.[39]
On January 28, 2015, the ACME protocol was officially submitted to the IETF for standardization.[40] On April 9, 2015, the ISRG and the Linux Foundation declared their collaboration.[19] The root and intermediate certificates were generated in the beginning of June.[24] On June 16, 2015, the final launch schedule for the service was announced, with the first certificate expected to be issued sometime in the week of July 27, 2015, followed by a limited issuance period to test security and scalability. General availability of the service was originally planned to begin sometime in the week of September 14, 2015.[41] On August 7, 2015, the launch schedule was amended to provide more time for ensuring system security and stability, with the first certificate to be issued in the week of September 7, 2015 followed by general availability in the week of November 16, 2015.[42] The cross-signature from IdenTrust is planned to be available when Let's Encrypt opens for the public.[23]
On September 14, 2015, Let's Encrypt issued its first certificate, which was for the domain helloworld
On October 19, 2015, the intermediate certificates became cross-signed by IdenTrust, causing all certificates issued by Let's Encrypt to be trusted by all major browsers.[22]
On November 12, 2015, Let's Encrypt announced that general availability would be pushed back and that the first public beta would commence on December 3, 2015.[44] The public beta ran from December 3, 2015[45] to April 12, 2016.[46]
On March 3, 2020, Let's Encrypt announced that it would have to revoke over 3 million certificates on March 4, due to a flaw in its Certificate Authority software.[47] Through working with software vendors and contacting site operators, Let's Encrypt was able to get 1.7 million of the affected certificates renewed before the deadline. They ultimately decided not to revoke the remaining affected certificates, as the security risk was low and the certificates were to expire within the next 90 days.[48]
In March 2020, Let's Encrypt was awarded the Free Software Foundation's annual Award for Projects of Social Benefit.[49]
Certificates issued
| Date | Certificates issued |
|---|---|
| March 8, 2016 | 1 million[50] |
| April 21, 2016 | 2 million[51] |
| June 3, 2016 | 4 million[52] |
| June 22, 2016 | 5 million[53] |
| September 9, 2016 | 10 million[54] |
| November 27, 2016 | 20 million[55] |
| December 12, 2016 | 24 million[56] |
| June 28, 2017 | 100 million[57] |
| August 6, 2018 | 115 million[58] |
| September 14, 2018 | 380 million[59] |
| October 24, 2019 | 837 million[60] |
| February 27, 2020 | 1 billion[61] |
See also
Further reading
References
- Aas, Josh (December 31, 2019). "Looking Forward to 2019". Let's Encrypt. Retrieved January 26, 2019.
- Kerner, Sean Michael (November 18, 2014). "Let's Encrypt Effort Aims to Improve Internet Security". eWeek.com. Quinstreet Enterprise. Retrieved February 27, 2015.
- Eckersley, Peter (November 18, 2014). "Launching in 2015: A Certificate Authority to Encrypt the Entire Web". Electronic Frontier Foundation. Retrieved February 27, 2015.
- Josh Aas; ISRG Executive Director. "Leaving Beta, New Sponsors". EFF. Retrieved April 12, 2016.
- Catalin Cimpanu. "Let's Encrypt Launched Today, Currently Protects 3.8 Million Domains". Softpedia News. Retrieved April 12, 2016.
- "How It Works". Let's Encrypt. Retrieved July 9, 2016.
- Tung, Liam (November 19, 2014). "EFF, Mozilla to launch free one-click website encryption". ZDNet. CBS Interactive.
- Fabian Scherschel (November 19, 2014). "Let's Encrypt: Mozilla und die EFF mischen den CA-Markt auf" (in German). heise.de.
- Marvin, Rob (November 19, 2014). "EFF wants to make HTTPS the default protocol". Software Development Times. BZ Media. Archived from the original on June 17, 2016. Retrieved May 27, 2019.
- Marier, Francois (January 1, 2015). "ITP: letsencrypt – Let's Encrypt client that can update Apache configurations". Debian Bug report logs.
- "python-letsencrypt". Debian Package Tracker. May 27, 2015.
- Barnes, Richard (April 30, 2015). "Deprecating Non-Secure HTTP". Mozilla Security Blog. Mozilla.
- "Marking HTTP As Non-Secure". The Chromium Projects.
- Moody, Glyn (November 25, 2014). "The Coming War on Encryption, Tor, and VPNs". Computerworld UK. IDG UK.
- Vaughan-Nichols, Steven J. (April 9, 2015). "Securing the web once and for all: The Let's Encrypt Project". ZDNet. CBS Interactive.
- https://www.theregister.com/2002/07/24/theres_certs_and_certs_verisign/
- Zorz, Zeljka (July 6, 2015). "Let's Encrypt CA releases transparency report before its first certificate". Help Net Security.
- Aas, Josh (March 13, 2018). "ACME v2 and Wildcard Certificate Support is Live". Let's Encrypt. Retrieved May 24, 2018.
- Kerner, Sean Michael (April 9, 2015). "Let's Encrypt Becomes Linux Foundation Collaborative Project". eWeek. QuinStreet Enterprise.
- "About Internet Security Research Group (ISRG)". letsencrypt.org. Archived from the original on March 9, 2020. Retrieved March 9, 2020.
- Aas, Josh (June 4, 2015). "Let's Encrypt Root and Intermediate Certificates". Let's Encrypt.
- Aas, Josh (October 19, 2015). "Let's Encrypt is Trusted".
- Reiko Kaps (June 17, 2015). "SSL-Zertifizierungsstelle Lets Encrypt will Mitte September 2015 öffnen" (in German). heise.de.
- Reiko Kaps (June 5, 2015). "Let's Encrypt: Meilenstein zu kostenlosen SSL-Zertifikaten für alle" (in German). heise.de.
- "Certificates". Let's Encrypt. Archived from the original on December 3, 2015.
- Aas, Josh (August 13, 2015). "Elliptic Curve Cryptography (ECC) Support". Let's Encrypt. Archived from the original on December 12, 2015.
- "Certificates". Let's Encrypt. Archived from the original on October 9, 2017.
- Brook, Chris (November 18, 2014). "EFF, Others Plan to Make Encrypting the Web Easier in 2015". Threatpost: The Kaspersky Lab Security News Service.
- "Draft ACME specification". GitHub. May 6, 2020.
- Barnes, Richard; Eckersley, Peter; Schoen, Seth; Halderman, Alex; Kasten, James (January 28, 2015). "Automatic Certificate Management Environment (ACME) draft-barnes-acme-01". Network Working Group.
- End of Life Plan for ACMEv1
- letsencrypt. "boulder/LICENSE.txt at master · letsencrypt/boulder · GitHub". Github.com. Retrieved January 6, 2016.
- 'Run Boulder inside your organization?' from Let's Encrypt user forum
- letsencrypt (November 23, 2015). "letsencrypt/LICENSE.txt at master · letsencrypt/letsencrypt · GitHub". Github.com. Retrieved January 6, 2016.
- Sanders, James (November 25, 2014). "Let's Encrypt initiative to provide free encryption certificates". TechRepublic. CBS Interactive.
- Aas, Josh (November 9, 2015). "Why ninety-day lifetimes for certificates?". Let's Encrypt. Retrieved June 26, 2016.
- "Let's Encrypt - Documentation".
- Aas, Josh (November 18, 2014). "Let's Encrypt | Boom Swagger Boom". Boomswaggerboom.wordpress.com. Archived from the original on December 8, 2015. Retrieved January 6, 2016.
- Joseph Tsidulko (November 18, 2014). "Let's Encrypt, A Free And Automated Certificate Authority, Comes Out Of Stealth Mode". crn.com. Retrieved August 26, 2015.
- History for draft-barnes-acme
- Josh Aas (June 16, 2015). "Let's Encrypt Launch Schedule". letsencrypt.org. Let's Encrypt. Retrieved June 19, 2015.
- "Updated Let's Encrypt Launch Schedule". August 7, 2015.
- Michael Mimoso. "First Let's Encrypt Free Certificate Goes Live". Threatpost.com, Kaspersky Labs. Retrieved September 16, 2015.
- "Public Beta: December 3, 2015". November 12, 2015.
- "Entering Public Beta - Let's Encrypt - Free SSL/TLS Certificates". Let's Encrypt. December 3, 2015. Retrieved January 6, 2016.
- "Let's Encrypt Leaves Beta". LinuxFoundation.org. Archived from the original on April 15, 2016. Retrieved April 17, 2016.
- "Revoking certain certificates on March 4". March 3, 2020. Retrieved March 4, 2020.
- Barrett, Brian. "The Internet Avoided a Minor Disaster Last Week". Wired. Conde Nast. Retrieved May 12, 2020.
- Let's Encrypt, Jim Meyering, and Clarissa Lima Borges receive FSF's 2019 Free Software Awards Free Software Foundation, 2020
- Aas, Josh (March 8, 2016). "Our Millionth Certificate - Let's Encrypt - Free SSL/TLS Certificates". letsencrypt.org. Retrieved March 15, 2016.
- "Let's Encrypt Reaches 2,000,000 Certificates". April 22, 2016. Retrieved September 24, 2016.
- "Let's Encrypt Stats". letsencrypt.org. June 5, 2016. Retrieved June 5, 2016.
- "Progress Towards 100% HTTPS, June 2016". letsencrypt.org. June 24, 2016. Retrieved June 22, 2016.
- Let's Encrypt [@letsencrypt] (September 9, 2016). "We've now issued more than 10 million certificates" (Tweet). Retrieved September 24, 2016 – via Twitter.
- Let's Encrypt [@letsencrypt] (November 27, 2016). "We've issued 20M+ certificates!" (Tweet). Retrieved November 27, 2016 – via Twitter.
- Let's Encrypt [@letsencrypt] (December 12, 2016). "Just over 1 year ago, we issued our first cert. Today, 24M+ and climbing!" (Tweet). Retrieved January 18, 2017 – via Twitter.
- "Milestone: 100 Million Certificates Issued - Let's Encrypt - Free SSL/TLS Certificates". letsencrypt.org. Retrieved July 2, 2017.
- "Let's Encrypt Root Trusted By All Major Root Programs". letsencrypt.org. Retrieved September 11, 2018.
- "Let's Encrypt on Twitter". Twitter. Retrieved September 16, 2018.
- "Let's Encrypt Growth Timeline". letsencrypt.org. Retrieved October 24, 2019.
- "Let's Encrypt Has Issued a Billion Certificates - Let's Encrypt - Free SSL/TLS Certificates". letsencrypt.org. Retrieved March 3, 2020.
External links
| Wikimedia Commons has media related to Let’s Encrypt. |