TLS termination proxy
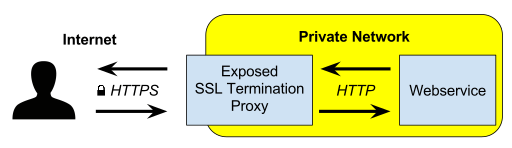
A TLS termination proxy (or SSL termination proxy[1]) is a proxy server that is used by an institution to handle incoming TLS connections, decrypting the TLS and passing on the unencrypted request to the institution's other servers (it is assumed that the institution's own network is secure so the user's session data does not need to be encrypted on that part of the link). TLS termination proxies are used to reduce the load on the main servers by offloading the cryptographic processing to another machine, and to support servers that do not support SSL, like Varnish.
A variant configuration is where encryption is done on the 'front-end' towards the Internet, and on the private 'back-end' network as well. This is generally referred to as "SSL/TLS forward proxy".[2][3][4] It is usually done to allow an intrusion detection system to analyze the traffic.
Another advantage of a forward TLS proxy is that it can reduce client latency if they would otherwise be geographically distant from the servers behind the proxy. This is because in most cases, with the exception of TLS1.3 0-RTT, there are several round trips involved in negotiating the TLS connection.
Servers capable of acting as a TLS/SSL termination proxy
- Apache HTTP Server
- Caddy (web server)
- Cloudflare's Flexible SSL[5]
- Envoy[6]
- F5 Networks' BIG-IP LTM load balancers
- HAProxy
- Hiawatha (web server)
- Hitch
- Nginx
- Pound (networking)
- Squid (software)
- stunnel
- Zorp firewall[7][8]
- Internet Information Services
References
- ↑ SSL Termination, F5 Networks.
- ↑ "SSL Forward Proxy Overview". Juniper Networks.
- ↑ "SSL Forward Proxy". Palo Alto Networks.
- ↑ "Overview: SSL forward proxy client and server authentication". F5 Networks.
- ↑ "What do the SSL options mean?". Cloudflare.
- ↑ "How to configure TLS termination in Envoy". Lyft.
- ↑ "How to configure HTTPS proxying in Zorp 6". Balabit.
- ↑ "Zorp Professional 6 Reference Guide". Balabit.